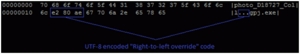
PRAGUE, CZECH REPUBLIC--(Marketwire - Sep 7, 2011) - "What you see is not what you get," thanks to a new wave of malware that misuses a special language display feature to trick people into opening supposedly "safe" files. The new exploit misuses features in Unicode -- the computing industry's standard for representing text -- to mask executable malware as "safe" files with a .doc or .jpg extension. It has been named "Unitrix" by AVAST Software analysts.
The Unicode feature is designed to display alphabets written in a right-to-left schema such as Arabic or Hebrew and flips the displayed text after special hidden codes such as 0x202E (right-to-left override) are added to the file name. For example, the executable malware file ending with "gpj.exe" is displayed to the recipient as the more innocent sounding "photo_D18727_Collexe.jpg".
"The typical user just looks at the extension at the very end of the file name; for example, jpg for a photo. And that is where the danger is," said Jindrich Kubec, head of the AVAST Virus Lab. "The only way a user can know this is an executable file is if they have some additional details displayed elsewhere on their computer or if a warning pops up when they try and execute the file."
The AVAST Virus Lab tracked a steady increase in the number of detections during August, with a daily peak of over 25,000. "From the email messages and the traffic pattern, this is clearly aimed at businesses," said Mr. Kubec. The attacks are almost exclusively made during the working week, with daily detections dropping below 5,000 on the weekend.
The most common Unitrix file is a malware downloader with connections to several URL addresses which then act as command and control centers. "Based on our analysis of over fifty samples, it appears to be part of a pay-per-install network with the capacity to send infected users a variety of malware," explains Mr. Kubec. Additional Unitrix information is on the AVAST blog.
"It is not possible to make a single universal, foolproof detection for it because this would create a lot of false positives, but there are definite ways to deal with this," said Mr. Kubec. He pointed out that avast! Antivirus end users are protected in two ways:
1. Simple detection when a file name using this trick appears on incoming mail.
2. Within the file system, avast! automatically suggests that the suspect file be opened in the sandbox, a safe virtualized environment.
"The problem is that this is a Unicode functionality. Although they mentioned the security implications of this in the specifications, people just implemented as designed and nobody cared about it. It's been mentioned in other antivirus lab sites but is not widely known," said Mr. Kubec.
ABOUT AVAST:
AVAST Software (www.avast.com) protects over 130 million active and 170 million registered users around the globe with its security and antivirus applications. Our portfolio includes the new avast! Business Protection for company networks, the premium avast! Internet Security with SafeZone™ virtualized desktop, avast! Pro Antivirus for customized computer protection needs and avast! Free Antivirus, the free computer security application that matches or exceeds the performance of other paid-for products. Anchored by the CommunityIQ network of sensors and supported by multiple protective shields, avast! performance is certified by VB100, ICSA Labs, and West Coast Labs.
Contact Information:
Contact:
Briana Papa
646-484-4573
Briana@crenshawcomm.com