PALO ALTO, CA--(Marketwired - May 17, 2016) - Hewlett Packard Enterprise (
The profile of typical cyber attackers -- and the interconnected nature of their underground economy -- have evolved dramatically in the last several years. Adversaries are increasingly leveraging sophisticated management principles in the creation and expansion of their operations to ultimately increase their impact and financial profits, which are both core motivations for nearly all attack groups today. Enterprises can use this inside knowledge against the attackers to disrupt the organizational structure and mitigate their risks.
"Organizations that think of cybersecurity as purely another checkbox to mark, often do not leverage the value in high fidelity cybersecurity intelligence," said Andrzej Kawalec (@digitalkawalec), Head of HPE Security Research and Chief Technology Officer, HPE Security Services, Hewlett Packard Enterprise. "This report gives us a unique perspective on how our adversaries operate and how we can disrupt them at each step of their criminal value chain."
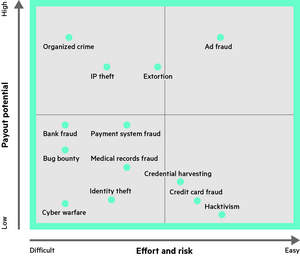
The Attackers' 'Value Chain'
Today's adversaries often create a formalized operating model and 'value chain' that is very similar to legitimate businesses in structure, and delivers greater ROI for the cybercriminal organization throughout the attack lifecycle. If enterprise-level security leaders, regulators and law enforcement are to disrupt the attackers' organization, they must first understand every step in the value chain of this underground economy.
Critical elements to the attackers' value chain models typically include:
- Human Resources Management - includes recruiting, vetting and paying the supporting 'staff' needed to deliver on specific attack requirements; the skills-based training and education of attackers also falls within this category.
- Operations - the 'management team' that ensures the smooth flow of information and funds throughout the attack lifecycle; this group will actively seek to reduce costs and maximize ROI at every step.
- Technical Development - the front-line 'workers' providing the technical expertise required to perform any given attack, including research, vulnerability exploitation, automation, and more.
- Marketing and Sales - these teams ensure that the attack group's reputation in the underground marketplace is strong and the illicit products are both known and trusted among the target audience of potential buyers.
- Outbound Logistics - this encompasses both the people and systems responsible for delivering purchased goods to a buyer, be it large batches of stolen credit card data, medical records, intellectual property or otherwise.
"Cybercriminals are highly professional, have robust funding, and are working together to launch concentrated attacks," said Chris Christiansen, Program Vice President, Security Products and Services, IDC. "The HPE Business of Hacking Report offers key insight for legitimate organizations to better disrupt adversaries and mitigate risks by understanding how they are operating and maximizing profits."
Disrupting the Chain and Advancing Enterprise Protection
HPE recommends a number of approaches for enterprise security professionals to better defend against these organized attackers:
- Reduce the Profits - Limit the financial rewards adversaries can realize from an attack on the enterprise by implementing end-to-end encryption solutions, such as HPE SecureData. By encrypting data at rest, in motion and in use, the information is rendered useless to the attackers, restricting their ability to sell and reducing profits.
- Reduce the Target Pool - The expansion of mobile and IoT has dramatically increased the possible attack surface for all enterprises. Organizations must build security into their development processes, and focus on protecting the interactions between data, apps and users regardless of device to better mitigate and disrupt adversary attacks.
- Learn from the Adversaries - New technologies such as 'deception grids' provide methods of trapping, monitoring and learning from attackers as they navigate their way through a realistic duplication of the network. Enterprises can use this information to better protect their real network, disrupt similar attacks before they begin, and slow down the progress of attackers.
Related Videos, Infographic and Webinar
- Business of Hacking Video: A discussion of "The Business of Hacking" and what it means for enterprises.
- Infographic: This timeline provides a short history of the enterprise security defenses developed to disrupt cyber attacks, and demonstrates why organizations must build security and analytics into their operations.
- Webcast: Register for the webcast on June 14 at 10:00 a.m. PT to hear HPE Security and IDC industry expert, Chris Christiansen, discuss what organizations are doing to effectively make themselves less of a target for cyber criminals, how security has evolved over time, and get a glimpse of what the future holds.
- Webcast: Cybercriminals - The unaddressed competition. Hear how HPE is digging into the world of cybercriminals to understand it and to disrupt it.
Methodology
The "Business of Hacking" leverages data and observations from HPE Security teams, open source intelligence, and other industry reports to deliver key insights into attackers' motivations, organizations and opportunities so that enterprises can better disrupt these activities and mitigate risks.
About HPE Security
HPE Security helps organizations protect their business-critical digital assets by building security into the fabric of the enterprise, detecting and responding to advanced threats, and safeguarding continuity and compliance to effectively mitigate risk. With an integrated suite of market-leading products, services, threat intelligence and security research, HPE Security empowers organizations to balance protection with innovation to keep pace with today's idea economy. Find out more about HPE Security at https://www.hpe.com/us/en/solutions/protect-digital.html.
Join HPE Software on LinkedIn and follow @HPE_Software on Twitter. To learn more about HPE Enterprise Security products and services on Twitter, please follow @HPE_Security and join HPE Enterprise Security on LinkedIn.
About Hewlett Packard Enterprise
Hewlett Packard Enterprise is an industry-leading technology company that enables customers to go further, faster. With the industry's most comprehensive portfolio, spanning the cloud to the data center to workplace applications, our technology and services help customers around the world make IT more efficient, more productive and more secure.
Forward-Looking Statement
This document contains forward-looking statements within the meaning of the safe harbor provisions of the Private Securities Litigation Reform Act of 1995. Such statements involve risks, uncertainties and assumptions. If such risks or uncertainties materialize or such assumptions prove incorrect, the results of Hewlett Packard Enterprise could differ materially from those expressed or implied by such forward-looking statements and assumptions. All statements other than statements of historical fact are statements that could be deemed forward-looking statements, including any statements of the plans, strategies and objectives of Hewlett Packard Enterprise for future operations; other statements of expectation or belief; and any statements of assumptions underlying any of the foregoing. Risks, uncertainties and assumptions include the possibility that expected benefits may not materialize as expected and other risks that are described in Hewlett Packard Enterprise's filings with the Securities and Exchange Commission, including but not limited to the risks described in Hewlett Packard Enterprise's Registration Statement on Form 10 dated July 1, 2015, as amended August 10, 2015, September 4, 2015, September 15, 2015, September 28, 2015 and October 7, 2015. Hewlett Packard Enterprise assumes no obligation and does not intend to update these forward-looking statements.
Contact Information:
Editorial contact
Evan Tamura
Hewlett Packard Enterprise
evan.tamura@hpe.com