NEW YORK and HERZLIYA, Israel, Oct. 5, 2015 (GLOBE NEWSWIRE) -- In today's ever-connected world, employees are using their devices for personal and business activities, and hackers are targeting these employees using enterprise cloud applications to distribute sophisticated malware. IT needs to combat this malicious activity with new and innovative solutions that are able to secure documents transferred via the cloud.
A photo accompanying this release is available at http://www.globenewswire.com/newsroom/prs/?pkgid=36657
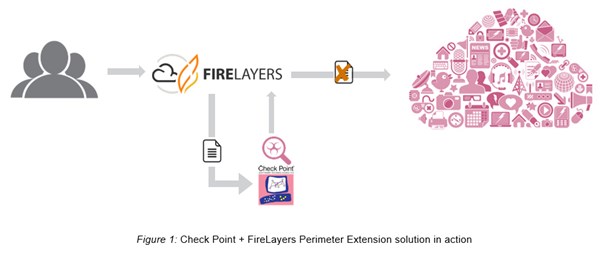
To halt these attacks in their tracks, FireLayers, which provides real-time protection for enterprise cloud applications, and Check Point Software Technologies, the largest pure-play security vendor globally, today announced their joint Extend Perimeter Security solution, which spreads security to cloud applications and provides enterprises with unprecedented protection from zero-day threats and malware distribution via these apps. In pairing the FireLayers Secure Cloud Application Platform with Check Point's SandBlast™ Threat Emulation service for advanced sandboxing, documents downloaded through file-sharing apps are scanned for and cleaned of any potential malicious behavior, ensuring the recipient of a document is not met by foul play.
"Today's organizations are increasingly dependent upon SaaS and the cloud and need the tools that will allow them to continue to be efficient and facilitate collaboration," said Alon Kantor, vice president, Business Development at Check Point. "Our Extend Perimeter Security solution will help organizations extend their security infrastructure to protect against many of the threats associated with SaaS application use today so that they can protect critical business information from any device."
As part of Extend Perimeter Security, the FireLayers Secure Cloud Application Platform scans all file repositories in the cloud, using Check Point SandBlast Threat Emulation to identify and detect any malware infected files. Depending upon the results of the scan, FireLayers enforces security policies to mitigate risk. The joint platform continuously evaluates all files at rest and as they are used. This includes malicious file uploads, shared file downloads, opening infected files and more, protecting the enterprise from active threats.
"We are excited to provide enterprises with a totally new level of much-needed protection against malware being distributed by cloud apps," said Boris Gorin, vice president, Security at FireLayers. "Today, enterprises need security solutions that can manage BYOD and anywhere/anytime access across the extended corporate network. FireLayers extends security protections to cloud app data, access and usage and delivers highly granular policy-based rule enforcement and auditing down to the single command level. The combined technologies from Check Point and FireLayers detect malware and prevent it from infiltrating organizations via cloud apps."
FireLayers protects enterprise cloud applications by integrating context and risk factoring into security policies and triggering user-facing mitigations to prevent data breaches. FireLayers proactively identifies file sharing related actions, in real time, in any application. This includes homegrown applications running on Azure, AWS and Google Cloud, among other IaaS (infrastructure-as-a-service) customized applications and off-the-shelf SaaS tools like Box, Google Apps, Office 365 and ServiceNow.
After intercepting files in transit or resting in document repositories, FireLayers, as part of the joint solution, delivers them to Check Point SandBlast Threat Emulation for inspection on premise or in the cloud. Check Point SandBlast inspects the file in a sandbox environment at the CPU level, evaluating whether the content is malicious or not. It then informs FireLayers of its analysis, triggering the following mitigations as needed: blocking, quarantine, admin alerts, user notifications or a combination of these actions.
Enterprises that deploy the Extend Perimeter Security solution derive the following benefits:
- Extending the perimeter: Widen their circle of protection off premise to include SaaS, IaaS and PaaS apps
- Secure collaboration: Safely leverage and empower collaboration with cloud-based platforms such as Office 365, Box, Dropbox, Jive, etc.
- Identifying and monitoring files: In real time, detect malicious content in cloud applications and mitigate risk with quarantines and alerts
- Preventing malicious uploads: Intercept malicious content before it is uploaded to cloud apps and notify administrators and users of risky behavior
- Enabling business: Real-time user mitigations and a transparent user experience reduce false positives and ensure cloud application usage remains uninterrupted
- Easy deployment: With no configuration on the client side, deployment is fast and seamless
For more information, download the Extend Perimeter Security solution brief or contact Jason Stolarczyk at Check Point via email at jstolarc@checkpoint.com; Ofer Smadari at FireLayers via email at ofers@firelayers.com.
| RESOURCES |
| Check Point + FireLayers Extend Perimeter Security Solution Brief |
| FireLayers Solution Datasheets |
| FireLayers LinkedIn |
| Come visit FireLayers at: |
| Data Connectors NYC Tech Security Conference, Oct. 15, 2015 |
| Boston Cyber Security Summit, Oct. 21, 2015 |
| CiConnect, Oct. 21, 2015 |
Tweet This: .@FireLayers prevents the spread of malware via cloud apps with @CheckPointSW http://bit.ly/1LlIRLG
ABOUT FIRELAYERS
FireLayers enables the responsible adoption of cloud apps, while ensuring security, compliance and governance of any cloud application on any device by any user. The FireLayers Secure Cloud Application Platform delivers full control over homegrown and popular apps like Salesforce, Office 365, SuccessFactors, NetSuite and endless others. Our Secure Cloud Application Platform, which features risk-based authentication, threat detection and user-centric threat prevention empowers enterprises with new levels of security, visibility and control across their cloud resources. FireLayers provides the granular control IT teams need to create safe zones for productive work while protecting enterprise data, networks and financial transactions from malicious attackers, external threats and accidental risky employee behavior.